ID: PMRREP20446| 211 Pages | 11 Dec 2025 | Format: PDF, Excel, PPT* | IT and Telecommunication

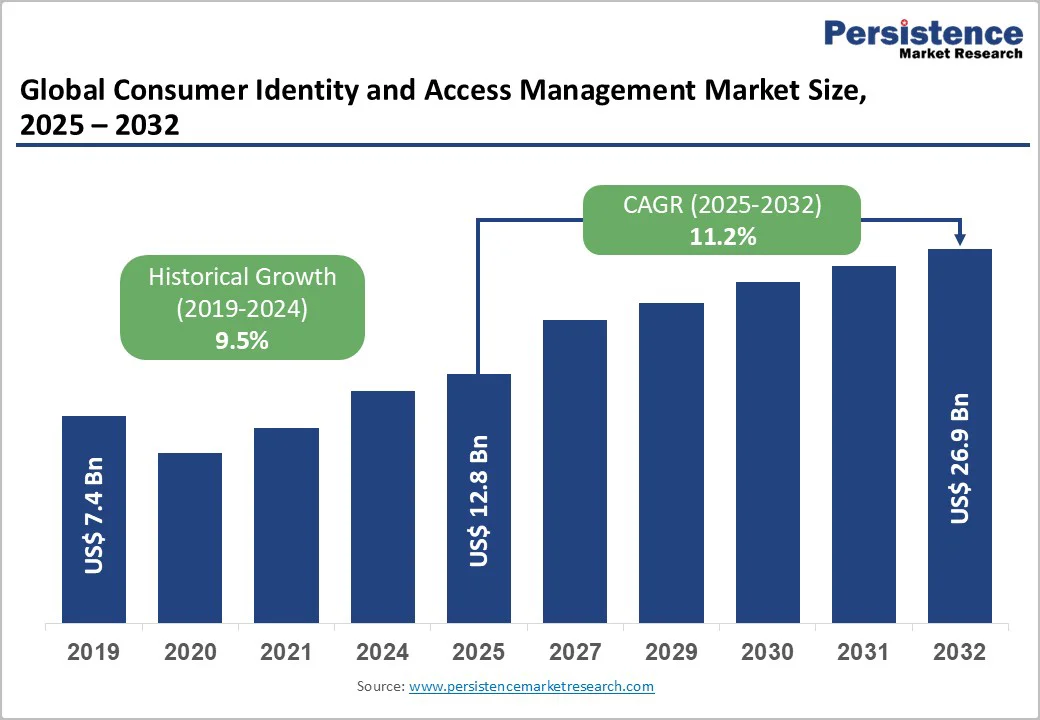
The global consumer identity and access management market size is valued at US$12.8 billion in 2025 and projected to reach US$26.9 billion by 2032, growing at a CAGR of 11.2% between 2025 and 2032.
The market expansion is fundamentally driven by escalating cybersecurity threats, with data breach costs averaging US$4.88 million in 2024, and by stringent regulatory compliance requirements, including GDPR, CCPA, and emerging regional data protection frameworks.
Rising consumer demand for secure digital experiences, coupled with organizational investments in zero-trust architecture and the deployment of multi-factor authentication across enterprise environments, creates compelling drivers for sustained market growth.
| Key Insights | Details |
|---|---|
| Consumer Identity and Access Management Market Size (2025E) | US$12.8 billion |
| Market Value Forecast (2032F) | US$26.9 billion |
| Projected Growth CAGR (2025 - 2032) | 11.2% |
| Historical Market Growth (2019 - 2024) | 9.5% |
Global enterprises are experiencing mounting cybersecurity risks, with the IBM Cost of a Data Breach Report 2024 identifying a worldwide average breach cost of US$ 4.88 million, underscoring severe financial and reputational consequences.
Compromised credentials remain the most frequent attack vector, generating average breach costs of roughly US$ 4.81 million, highlighting the critical need for stronger consumer authentication and access controls. India continues to report one of the highest breach costs globally at INR 220 million (INR 22 crore), reflecting regional vulnerability and accelerating demand for advanced CIAM deployments.
Financial services organizations face even greater exposure, with average breach costs exceeding US$ 6 million, driven by sensitive customer data and heightened account takeover threats. These pressures are compelling organizations to invest in CIAM platforms featuring multi-factor authentication, adaptive risk scoring, and real-time threat analytics, which deliver measurable returns through breach avoidance, regulatory compliance, and stronger consumer trust.
Regulatory frameworks, including the General Data Protection Regulation (GDPR), California Consumer Privacy Act (CCPA), and emerging data protection regulations globally, mandate comprehensive identity governance, consent management, and consumer data protection mechanisms.
GDPR compliance requirements impose strict penalties exceeding €20 million or 4% of annual turnover for substantive violations, creating compelling financial justification for identity management system implementation.
CCPA and California Privacy Rights Act (CPRA) establish consumer rights regarding personal data access, deletion, and disclosure, requiring organizations to implement identity proofing services and access control mechanisms enabling consumer self-service identity verification and data management.
Financial institutions operating across multiple jurisdictions face converging regulatory requirements mandating strong customer authentication (SCA) for payment transactions, driving widespread multi-factor authentication deployment and identity verification system adoption. Healthcare organizations comply with HIPAA regulations requiring comprehensive audit trails and identity-based access controls for patient data protection.
Public administration agencies implementing digital government initiatives increasingly require citizens to establish verified digital identities through standardized identity proofing services and authentication mechanisms. These regulatory mandates establish baseline consumer identity management adoption across all industry verticals, creating sustained demand drivers independent of cyclical business conditions.
Implementing consumer identity and access management systems often introduces extensive technical and organizational complexity, particularly for enterprises operating on legacy authentication and directory infrastructures. Integrating modern CIAM platforms with existing repositories, custom applications, and governance workflows requires advanced middleware, data mapping, and system reconfiguration, increasing project timelines and costs.
Transitioning to multi-factor or passwordless authentication further demands user training, communication plans, and support structures to ensure smooth adoption. Organizations shifting toward zero-trust architectures must simultaneously update access control policies, identity workflows, and monitoring systems, adding operational strain.
Migration from on-premise models to cloud SaaS raises data residency and compliance concerns, especially in regulated industries. Misconfiguration risks, incomplete migrations, and skill shortages amplify hesitation, slowing enterprise-wide CIAM modernization.
Data Privacy Concerns and Cybersecurity Risks Associated with Centralized Identity Repositories
Centralized CIAM platforms aggregate large volumes of sensitive consumer data, creating high-value targets for cyberattacks and driving significant privacy and security concerns. Strict regulations increasingly require transparent consent management, limited data retention, and auditable processing workflows, raising compliance burdens for organizations.
Sophisticated threat actors frequently target identity systems because they can grant access across multiple interconnected applications, increasing the risk of account takeover, credential compromise, and large-scale data breaches. Storing authentication credentials, biometrics, and personal profiles in a single repository magnifies the impact of security incidents, often resulting in severe financial penalties and reputational damage.
To mitigate risk, organizations must implement advanced safeguards such as encryption, continuous behavioral analytics, and intrusion detection, substantially increasing operational costs. Heightened consumer privacy sensitivities further constrain adoption in regions where trust in digital identity systems remains limited.
Passwordless authentication technologies, including biometric authentication, hardware security keys, and push-based approval mechanisms, represent the fastest-growing consumer identity authentication segment, with an anticipated CAGR exceeding 15.2% through 2032.
Organizations increasingly recognize that password-based authentication represents the weakest component in identity security architecture, motivating comprehensive transitions to passwordless approaches supporting superior security outcomes and improved user experience.
Biometric authentication technologies, including fingerprint, facial recognition, and behavioral biometrics, offer convenience while delivering security improvements over traditional password approaches.
Financial institutions implementing payment authentication increasingly deploy biometric authentication for transaction authorization, driving substantial adoption across banking, payment, and e-commerce verticals. Regulatory frameworks, including GDPR and emerging digital identity regulations, increasingly mandate strong authentication mechanisms, creating policy-driven demand for passwordless and biometric approaches.
Consumer preference for frictionless authentication experiences strongly favors passwordless approaches, with adoption rates increasing across consumer demographics. Enterprises investing in a passwordless authentication framework position themselves for a competitive advantage through a superior security posture and enhanced consumer satisfaction metrics.
The zero-trust architecture paradigm fundamentally redesigns enterprise security around identity verification and continuous authentication, with identity and access management as critical architectural components.
Organizations globally recognize that traditional perimeter-based security approaches provide insufficient protection against sophisticated threat actors operating within enterprise networks, motivating comprehensive shifts toward zero-trust architecture deployment.
Cloud computing adoption and distributed workforce models increase the complexity of traditional access control approaches, creating compelling justification for a zero-trust architecture implementing identity-centric security verification.
Implementation of zero-trust architecture requires a comprehensive CIAM platform with capabilities enabling granular access control, attribute-based access policies, and continuous authentication verification. Organizations implementing zero-trust architecture report substantial security improvements, including reduced breach incidents, faster threat detection, and improved audit trail documentation supporting regulatory compliance.
Government agencies globally, including the United States Cybersecurity and Infrastructure Security Agency (CISA), actively promote zero-trust architecture adoption across enterprise environments, creating policy-driven market demand, and accelerating technology adoption across private and public sector organizations.
Identity Administration and Authentication remains the dominant component segment, holding about 38% market share in 2025 due to its essential role in securing all consumer-facing digital interactions. These capabilities support core functions such as account creation, user verification, multi-factor authentication, and access policy enforcement, forming the foundational layer of every CIAM deployment.
Organizations rely on this segment to maintain compliance, reduce fraud risk, and streamline customer onboarding across diverse digital channels. As digital ecosystems expand, Identity Administration and Authentication increasingly integrates with advanced analytics and governance tools, enabling contextual risk assessment and dynamic access control.
Rising cyber threats and regulatory scrutiny continue to reinforce the segment’s centrality to modern identity frameworks.
On-premise deployment leads the global CIAM market with roughly 52% share in 2025, supported by stringent data residency, privacy, and compliance mandates across sectors like finance, healthcare, and government. Organizations in these regulated environments prefer on-premise models because they enable full control over sensitive consumer data, tighter infrastructure oversight, and deep customization aligned with legacy system architectures.
This deployment model is also favored for high-security use cases requiring strict auditability and minimal third-party dependency. Despite growing cloud adoption, on-premise CIAM remains the backbone for institutions balancing identity modernization with regulatory obligations. Its continued relevance reflects the need for sovereignty, security assurance, and tailored integration in mission-critical environments.
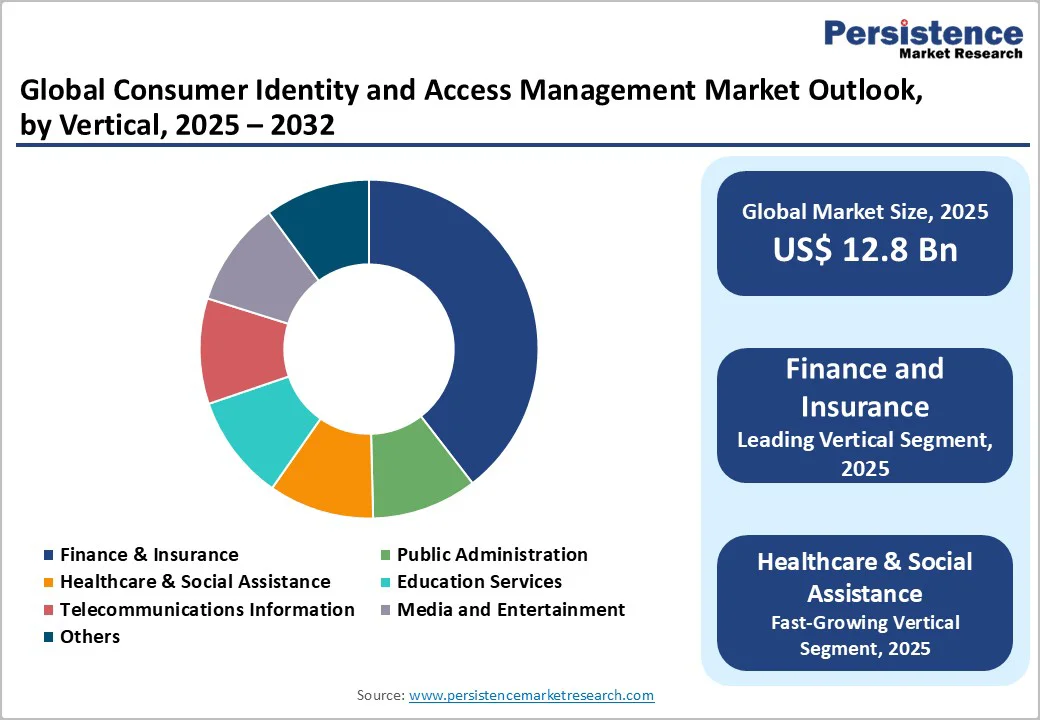
Finance and Insurance constitutes the leading vertical segment, capturing approximately 35% market share in 2025, due to its heightened exposure to cyberattacks and stringent regulatory frameworks governing customer identity verification. Financial institutions depend on CIAM solutions to meet KYC and AML compliance, safeguard high-value transactions, and prevent identity fraud through advanced authentication and identity proofing mechanisms.
The segment’s reliance on secure digital channels for payments, lending, and investment services further accelerates CIAM adoption, particularly as mobile banking and fintech platforms expand. Continuous regulatory updates and the need for frictionless yet secure customer experiences ensure sustained investment, positioning Finance and Insurance as the most mature and security-intensive adopter of CIAM technologies.
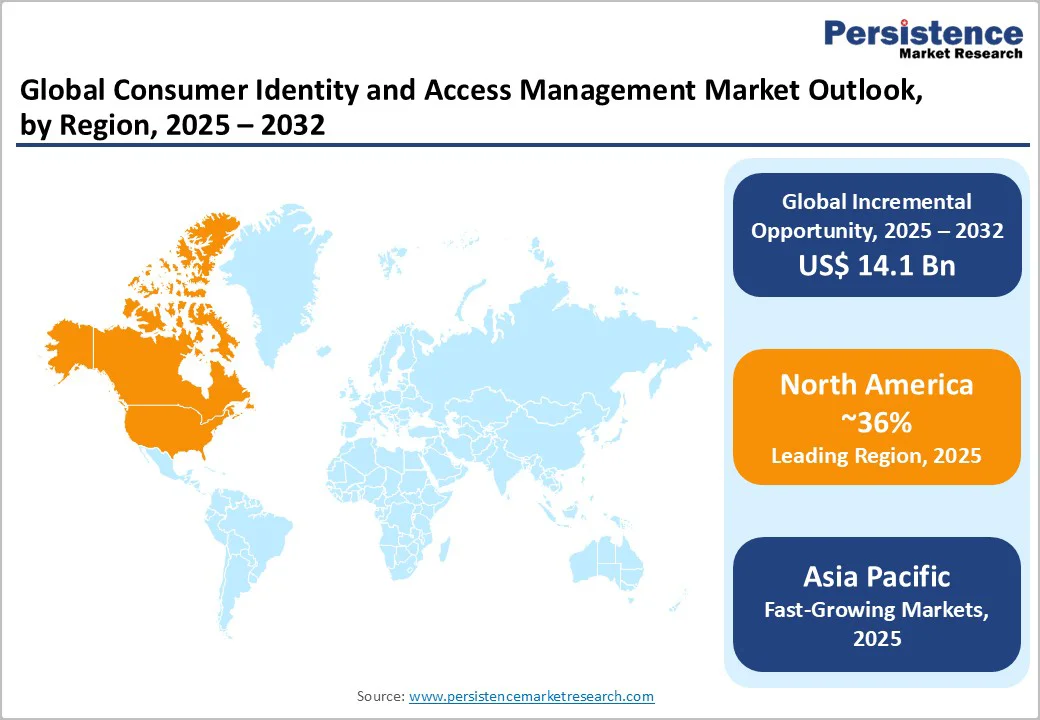
North America maintains market leadership with approximately 36% of the global consumer identity and access management market share in 2025, driven by strong regulatory frameworks, mature digital economy, and substantial cybersecurity investment requirements.
The United States regulatory environment, including CCPA, CPRA, and sector-specific requirements such as HIPAA and financial services regulations, mandates comprehensive consumer identity management across industry verticals.
Major technology leaders headquartered in North America, including IBM, Microsoft, Okta, and Salesforce drive innovation in consumer identity management technology, supporting regional leadership in platform capabilities and service delivery sophistication.
Financial services institutions across North America implement sophisticated identity proofing and authentication systems supporting compliance with Federal Financial Institutions Examination Council (FFIEC) guidance on authentication and fraud prevention. Healthcare system digital transformation initiatives accelerate CIAM adoption, particularly supporting telehealth service authentication and patient portal access management.
The Canadian market exhibits comparable regulatory requirements to the United States through the Personal Information Protection and Electronic Documents Act (PIPEDA), supporting consistent market adoption patterns.
U.S. federal government agencies increasingly implement zero-trust architecture and identity-centric security frameworks, with identity and access management representing critical components of cybersecurity modernization initiatives. Enterprise technology investments in cybersecurity continue to expand, with identity management representing a priority expenditure category that supports breach-prevention objectives.
Europe represents the second-largest regional market, driven by the GDPR regulatory framework, which establishes comprehensive data protection standards and consumer identity governance requirements.
Germany maintains its position as Europe's largest economy and CIAM adopter, with organizations implementing comprehensive identity governance supporting GDPR compliance and consumer data protection. United Kingdom organizations continue GDPR compliance despite Brexit, with UK-GDPR establishing equivalent data protection requirements supporting consumer identity management investments.
France and Spain implement GDPR compliance frameworks alongside national data protection regulations, requiring organizations to implement identity-centric security architectures supporting regulatory mandates. European data protection authorities aggressively enforce GDPR compliance, generating substantial penalties, motivating organizational investments in compliant identity and access management systems.
The European Union's digital identity initiative, which promotes standardized digital wallet and identity verification approaches, supports market expansion potential through interoperable identity infrastructure development. Financial institutions across European member states implement strong customer authentication requirements supporting Payment Services Directive compliance through multi-factor authentication and identity verification mechanisms.
Asia-Pacific represents the fastest-growing regional market with a projected CAGR exceeding 14.8% through 2032, driven by rapid digital economy expansion, emerging regulatory frameworks, and increasing cybersecurity threat exposure.
China implements a comprehensive national digital identity infrastructure supporting digital government services, e-commerce authentication, and financial system compliance. India's digital identity ecosystem including the Aadhaar biometric identification system supports identity proofing capabilities across financial inclusion, government services, and consumer authentication applications.
Japan maintains a sophisticated digital payment infrastructure requiring advanced consumer identity verification, supporting e-commerce authentication and payment security. ASEAN countries, including Vietnam, Thailand, and Malaysia, implement emerging data protection regulations, motivating organizational CIAM adoption, particularly within financial services and e-commerce verticals.
Government digital transformation initiatives across Asian-Pacific nations increasingly incorporate digital identity and authentication components, supporting market expansion potential through public sector investments.
The global consumer identity and access management market is moderately consolidated, shaped by a mix of large technology ecosystems and specialized identity platforms. Market structure increasingly favors vendors with cloud-native architectures, scalable SaaS delivery, and deep integration capabilities across enterprise applications.
Competitive strategies focus on expanding zero-trust frameworks, enhancing authentication intelligence, and incorporating machine learning for real-time risk assessment.
Companies pursue mergers and acquisitions to consolidate niche identity technologies, strengthen product portfolios, and accelerate global reach. Growing demand for simplified deployment drives expansion of managed and IDaaS models, while differentiation increasingly depends on advanced analytics, interoperability, regulatory compliance alignment, and frictionless user experience delivery.
The global consumer identity and access management market is valued at US$ 12.8 billion in 2025 and is projected to reach US$ 26.9 billion by 2032 at a CAGR of 11.2%.
The market is driven by rising data breach costs, expanding global privacy regulations, rapid zero-trust architecture adoption, widespread multi-factor authentication deployment, and growing consumer demand for secure digital interactions.
Identity Administration and Authentication leads the market with 38% share in 2025, supported by its universal necessity across all consumer-facing applications.
Asia-Pacific is the fastest-growing region with CAGR above 14.8% through 2032, driven by digital economy expansion and strengthening data protection regulations.
Passwordless and biometric authentication represents the biggest opportunity as organizations adopt frictionless, secure authentication aligned with regulatory expectations and mobile-first user behavior.
Major leaders include Microsoft, Okta, IBM, Ping Identity, SAP, and Salesforce, supported by strengths in cloud-native platforms, AI-driven security, and enterprise integration capabilities.
| Report Attribute | Details |
|---|---|
| Historical Data/Actuals | 2019 - 2024 |
| Forecast Period | 2025 - 2032 |
| Market Analysis Units | Value: US$ Mn/Bn, Volume: As Applicable |
| Geographical Coverage |
|
| Segmental Coverage |
|
| Competitive Analysis |
|
| Report Highlights |
|
By Component Type
By Deployment
By Vertical
By Location
By Regions
Delivery Timelines
For more information on this report and its delivery timelines please get in touch with our sales team.
About Author