ID: PMRREP15901| 190 Pages | 21 Apr 2025 | Format: PDF, Excel, PPT* | IT and Telecommunication

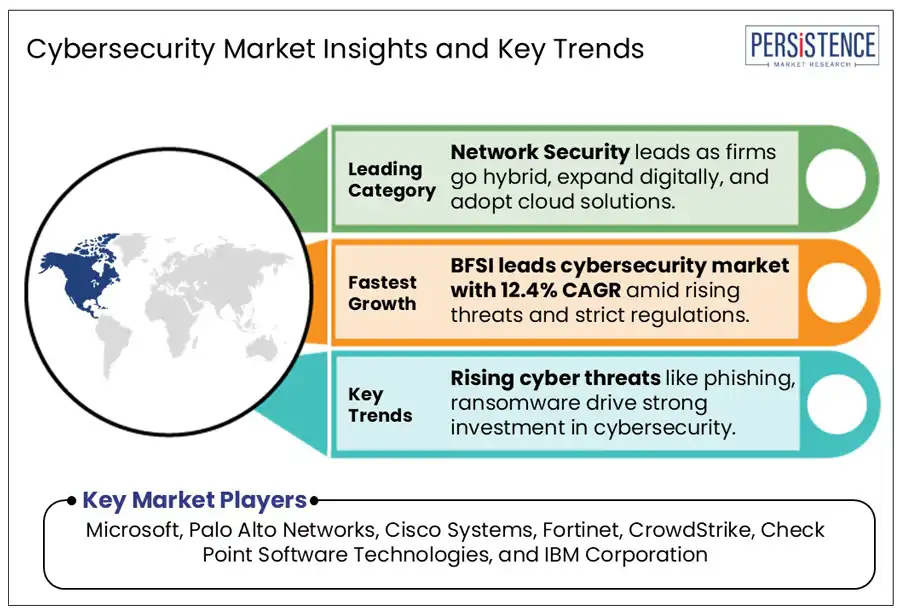
The global cybersecurity market was valued at US$ 225.7 Bn in 2025, and expected to reach US$ 443.1 Bn growing at a CAGR of 10.2% by 2032.
Cybersecurity implies the protection of internet-connected systems, including hardware, software, and data, from cyber threats such as hacking, malware, phishing, and other malicious activities. It involves implementing processes, technologies, and controls to safeguard networks, devices, and sensitive information. The primary objective of cybersecurity is to maintain the confidentiality, integrity, and availability of information by preventing, detecting, and responding to security incidents.
Several factors are driving the growth of cybersecurity market, owing to increasing adoption of connected devices and systems, which expands the attack surface and encourages stronger security measures. Additionally, the rising frequency and severity of cyberattacks are exposing vulnerabilities in networks and systems, further increasing the demand for robust cybersecurity solutions.
Additionally, stringent data privacy regulations, such as the EU's General Data Protection Regulation (GDPR), require organizations to implement strong security measures to protect personal data. Similarly, China’s Cybersecurity Law and India’s Digital Personal Data Protection Act (DPDP) impose stringent data security requirements on businesses operating within these regions. With stricter regulations in place, businesses are investing more in cybersecurity to stay compliant, protect against cyber threats, and maintain customer trust.
In terms of the regional market, North America accounted for a leading market share of 34.7% in the global landscape in 2024. Meanwhile, demand for cybersecurity in the Europe region will account for a market share of 25.1% in 2025.
|
Global Attribute |
Key Insights |
|
Cybersecurity Market Size (2025) |
US$ 225.7 Bn |
|
Projected Market Value (2032) |
US$ 443.1 Bn |
|
Global Market Growth Rate (2025-2032) |
10.2% |
|
Network Security Segment Market Share (2024) |
32.7% |
|
India Market Growth Rate (2025-2032) |
13.9% |
|
BFSI Segment Market Growth Rate (2025-2032) |
12.4% |
The increasing frequency and sophistication of cyber threats have become key factors driving the rapid growth of the global cybersecurity market. As hackers develop more advanced techniques, organizations and governments are ramping up their investments to protect critical data and infrastructure.
In the U.K., the cybersecurity sector generated USD 17.5 billion in revenue in 2024 an impressive 12% increase from the previous year. With over 2,165 active firms and a workforce of 67,300, the Gross Value Added (GVA) in cybersecurity has surged by 21% to USD 10.3 billion. The UK's National Cybersecurity Centre (NCSC) reported a 16% rise in cyber incidents in 2024, totaling 430 cases compared to 371 in the previous year. This rapid expansion is fueled by a sharp growth in cyberattacks including high-profile incidents that have disrupted essential services such as London hospitals and the British Library.
The United States is also facing a rise in cyber threats with ransomware attacks soaring by over 70% between 2022 and 2023, according to CISA (Cybersecurity and Infrastructure Security Agency). Critical infrastructure and businesses are increasingly under siege, prompting massive investments in cybersecurity. This growing urgency to safeguard critical assets, scales the cybersecurity market to new heights.
The shortage of skilled cybersecurity professionals is a growing challenge for businesses worldwide. According to the 2024 ISC2 Cybersecurity Workforce Study, the industry faces a shortfall of 4.8 million professionals marking a 19% increase from the previous year. This widening talent gap makes it increasingly difficult for organizations to find qualified experts in ethical hacking, penetration testing, and incident response, critical roles in defending against evolving cyber threats.
Without adequate expertise, businesses face a heightened risk of security breaches, which can be financially devastating. The 2024 report on Cost of a Data Breach by IBM estimates that the average data breach now costs US$4.9 million, reflecting a 10% increase from the previous year. This financial burden is particularly challenging for small and medium-sized enterprises (SMEs), which often struggles to afford cybersecurity solutions, making them prime targets for cybercriminals.
In March 2024, the National Cybersecurity Strategy is reshaping how the public and private sectors approach cybersecurity. By prioritizing a resilient digital ecosystem, the strategy pushes for investments in cutting-edge cybersecurity technologies, fueling industry growth. Financially, the U.S. government is making bold commitments the Department of Defense (DoD) allocated $58.5 billion for IT and cybersecurity in the FY24 budget, with $13.5 billion dedicated to cyber investments and $45 billion for both unclassified and classified IT projects. This not only strengthens national security but also creates a booming demand for cybersecurity solutions.
Government agencies are also stepping up their cybersecurity game. The Cybersecurity and Infrastructure Security Agency (CISA), with a $3 billion budget for 2025, is actively working to protect critical infrastructure, boosting procurement of security tools. Meanwhile, federal mandates like the Zero Trust Strategy are pushing agencies to adopt advanced security frameworks, accelerating demand for Zero Trust Architecture (ZTA) solutions. These combined efforts are driving unprecedented growth in the cybersecurity market, fueling a surge in innovations and investments.
These factors are creating lucrative opportunities for the adoption of cybersecurity systems in the U.S., contributing to its significant 28.6% share of the global market in 2025.
?Asia Pacific (APAC) is experiencing rapid growth in cybersecurity due to increasing digital transformation, widespread mobile connectivity, and rising cyber threats. Countries such as China, India, and Japan have witnessed a surge in internet penetration and mobile device usage, expanding the digital landscape and necessitating stronger cybersecurity measures to protect sensitive data and maintain trust in digital systems.
With industries such as manufacturing, healthcare, and finance integrating IoT solutions, the attack surface for cyber threats is expanding, making cybersecurity a critical component of business operations. Governments are also prioritizing cybersecurity as seen in Thailand’s goal to expand its digital economy to 30% of GDP by 2030. Additionally, major global tech investments such as Oracle’s US$6.5 billion cloud expansion in Malaysia, highlight APAC's strategic importance in the cybersecurity. Such factors are majorly contributing to ushering in the growth of the India cybersecurity market at a CAGR of 13.9% during the forecast period.
Network security segment is analysed to have the major market share of 32.7% in 2024, driven by the escalating complexity and frequency of cyber threats targeting organizational infrastructures. As cyber adversaries develop more sophisticated methods, the imperative to protect network integrity has intensified, prompting substantial investments in network security solutions.
The rise of cloud computing & remote work has made securing sensitive data across multiple locations a major challenge. Companies need strong network security to ensure safe access for employees and protect critical systems. As more organizations embrace flexible work models, the demand for robust network security continues to grow, reinforcing its position as a leader in the cybersecurity market.
The BFSI (Banking, Financial Services, and Insurance) industry is expected to grow at the highest CAGR of 12.4% during the forecast period. With vast amounts of sensitive customer data and high-value transactions happening every second, financial institutions have become prime targets for cybercriminals.
With the increasing digitization of transactions, cyber threats such as hacking, phishing, malware, and ransomware have become more sophisticated, increasing the demand for advanced cybersecurity solutions.
With cyber threats becoming more sophisticated, major financial institutions are making massive investments in security. For example, JPMorgan Chase has boosted its technology budget by US$1.5 billion, bringing the total to a staggering US$17 billion in 2024. At the same time, Bank of America has spent US$4 billion to bolster cybersecurity to ensure regulatory compliance, and enhance customer experience.
The global cybersecurity market is fragmented. Industries adopt automation and interconnected systems as cybersecurity vendors prioritize embedding strong security measures into their products. This enhances system protection and appeals to security-conscious customers. For instance, the National Institute of Standards and Technology (NIST) emphasized the need to address vulnerabilities in Industry 4.0 to ensure operational security. Meanwhile, mergers and acquisitions became a key strategy as larger vendors sought growth and market consolidation. With startup funding uncertain, many smaller firms perceive M&A as a viable opportunity to stay competitive.
Recent developments related to key players providing market solutions have been tracked by the analysts at Persistence Market Research, which will be accessible in the full report.
The global market is projected to be valued at US$ 225.7 Mn in 2025.
Rising frequency and sophistication of cyberattacks are the key market drivers.
The market is poised to witness a CAGR of 10.2% from 2025 to 2032.
The rapid adoption of cloud computing, IoT, AI/ML technologies, and the shift to remote and hybrid work environments is a key market opportunity.
Microsoft, Broadcom, Cisco Systems, Palo Alto Networks, and Fortinet are among the leading key players.
|
Report Attribute |
Details |
|
Historical Data/Actuals |
2019 - 2024 |
|
Forecast Period |
2025 - 2032 |
|
Market Analysis Units |
Value: US$ Bn/Mn |
|
Key Regions Covered |
|
|
Segmental Coverage |
|
|
Competitive Analysis |
|
|
Report Highlights |
|
|
Customization and Pricing |
Available upon request |
By Component:
By Security Type:
By Deployment:
By Enterprise Size:
By Industry:
By Region:
Delivery Timelines
For more information on this report and its delivery timelines please get in touch with our sales team.
About Author