ID: PMRREP32671| 197 Pages | 30 Dec 2025 | Format: PDF, Excel, PPT* | IT and Telecommunication

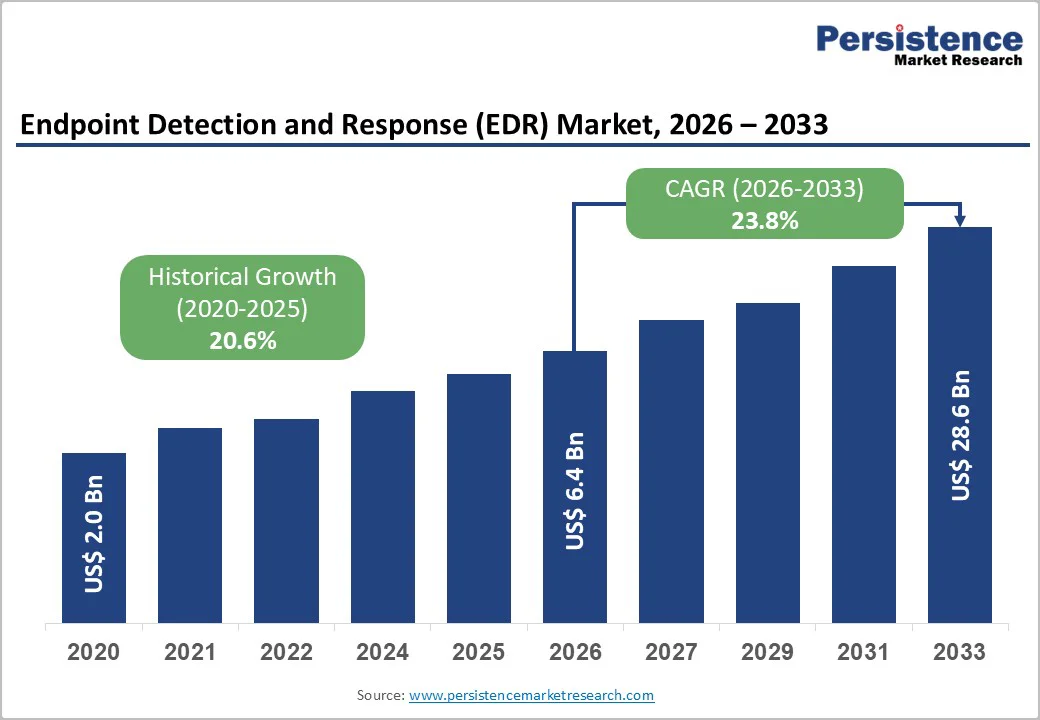
The global Endpoint Detection and Response (EDR) Market size is projected to rise from US$ 6.4 Bn in 2026 to US$28.6 Bn by 2033. It is anticipated to witness a CAGR of 23.8% during the forecast period from 2026 to 2033. This exceptional growth trajectory is driven by the convergence of escalating cyber threats, stringent regulatory compliance requirements, and ongoing enterprise digital transformation initiatives. Ransomware attacks have surged significantly, while the proliferation of hybrid and remote work models has fundamentally expanded the enterprise attack surface. In addition, regulatory frameworks such as GDPR, HIPAA, CCPA, and CMMC mandate robust endpoint monitoring and response capabilities across key sectors, including finance, healthcare, and government.
| Key Insights | Details |
|---|---|
|
Endpoint Detection and Response (EDR) Market Size (2026E) |
US$6.4 Bn |
|
Market Value Forecast (2033F) |
US$28.6 Bn |
|
Projected Growth (CAGR 2026 to 2033) |
23.8% |
|
Historical Market Growth (CAGR 2020 to 2025) |
20.6% |
Driver
The frequency and complexity of endpoint-targeted attacks have reached unprecedented levels, with ransomware representing one of the most damaging threat vectors. Ransomware attacks more than doubled between 2020 and 2021, reflecting a sharp escalation in both attack frequency and operational sophistication as organizations rapidly shifted to remote work environments. Since then, ransomware activity has continued to rise steadily, with year-over-year growth rates typically ranging between 30% and 40% through 2025, driven by the proliferation of ransomware-as-a-service (RaaS) models, the expansion of enterprise attack surfaces, and higher financial incentives for threat actors. Modern ransomware operates with devastating speed, capable of encrypting entire network environments within 60 minutes. Organizations without mature EDR deployments experience successful endpoint infections at rates 5x higher than those with EDR solutions in place.
The permanent shift to hybrid and remote work has fundamentally transformed endpoint security requirements. Organizations now operate distributed workforces where endpoints access corporate resources from unsecured home networks, personal WiFi connections, and diverse geographic locations outside traditional perimeter defenses. This expansion has increased the attack surface exponentially: each remote employee represents an additional endpoint vulnerable to compromise, lateral movement, and data exfiltration. The proliferation of bring-your-own-device (BYOD) policies further compounds this risk, as personal devices integrate with corporate networks without the visibility and control of managed enterprise equipment.
Restraint
Organizations must navigate integration challenges when EDR solutions interact with legacy security infrastructure, create alert management protocols to prevent alert fatigue from false positives, and develop incident response procedures that translate automated threat detection into appropriate remediation actions. The cybersecurity talent shortage exacerbates this challenge organizations cannot recruit sufficient personnel to operate sophisticated EDR platforms effectively, necessitating either expensive external managed detection and response (MDR) services or accepting operational risk from underutilized solutions.
EDR deployment has become economically justified at the enterprise level, but the direct acquisition and operational costs remain substantial barriers for small and medium enterprises (SMEs). Beyond software licensing, organizations must fund implementation services, user training, integration with existing security tools, and ongoing operational support. For SMEs with limited IT budgets, these cumulative costs represent significant capital commitments, particularly when competing against traditional vulnerability management and basic endpoint protection solutions that occupy existing budget allocations.
Opportunity
The emergence of managed detection and response (MDR) business models addresses both the talent shortage and implementation complexity constraints that limit traditional EDR adoption. In the MDR model, organizations outsource endpoint monitoring, threat hunting, and incident investigation to specialized service providers operating 24/7 threat monitoring centers. This addresses the capability gap for organizations lacking dedicated security operations centers while distributing costs across a customer base, improving unit economics. Sophos reported a 37% increase in MDR customer base in 2024, and this growth trajectory appears sustainable as organizations increasingly prioritize outcome-based security engagement over point solution procurement.
Organizations increasingly recognize that EDR solutions, while essential, provide incomplete threat visibility when attackers leverage multi-vector campaigns involving network intrusion, email compromise, cloud account takeover, and identity exploitation in coordinated sequences. Extended Detection and Response (XDR) platforms unify endpoint, network, cloud, identity, and third-party security data into integrated threat detection and response workflows, enabling detection of sophisticated attack patterns that isolated endpoint telemetry misses. The platform migration creates both upgrade opportunities with existing customer bases and greenfield opportunities where organizations can select XDR-native architecture rather than layering detection and response tools across legacy infrastructure.
Solution Analysis,
Software dominates the market, representing over 63% of the 2026 market value at US$ 4.0 Bn. This dominance reflects the necessity of agent-based endpoint monitoring and the criticality of detection and investigation capabilities in the EDR value proposition. It integrates antivirus, behavioral analysis, and advanced threat detection into unified agent architectures. Large enterprises particularly favor comprehensive software platforms from established vendors that offer extensive feature sets, threat intelligence integration, and development ecosystems for customization.
Services represent the fastest-growing segment, expanding at 25.9% CAGR through 2033, with particular emphasis on managed detection and response engagements. Services encompass implementation and integration support, ongoing operational management, custom threat hunting focused on organization-specific threat actors and attack patterns, and incident response coordination during active compromise scenarios. The services opportunity extends beyond pure-play EDR vendors to managed security service providers (MSSPs), consulting firms specializing in cybersecurity, and technology solution providers integrating EDR services into broader managed security offerings.
Deployment Analysis,
Cloud-based, representing 56% of the 2026 market value at US$ 3.6 Bn, reflects fundamental architectural advantages in managing distributed endpoint populations. It eliminates capital expenditure requirements for infrastructure, reduces complexity of on-premises operations center management, and provides inherent scalability to accommodate endpoint population growth without proportional infrastructure investment. Organizations migrating from on-premises infrastructure to cloud-based operations benefit from elimination of update management complexity, simplified licensing and enhanced integration with cloud workload protection and identity security solutions operating in similar cloud infrastructure.
On-premises while declining as a share of new deployments, remains critical for organizations with legacy infrastructure requirements, air-gapped network architectures, or extreme security posture requirements. Government agencies and defense contractors frequently mandate on-premises EDR deployment without external connectivity to protect classified information and operational security. Manufacturing organizations with operational technology integration requirements often prefer on-premises solutions providing direct control of endpoint data and forensic evidence collection.
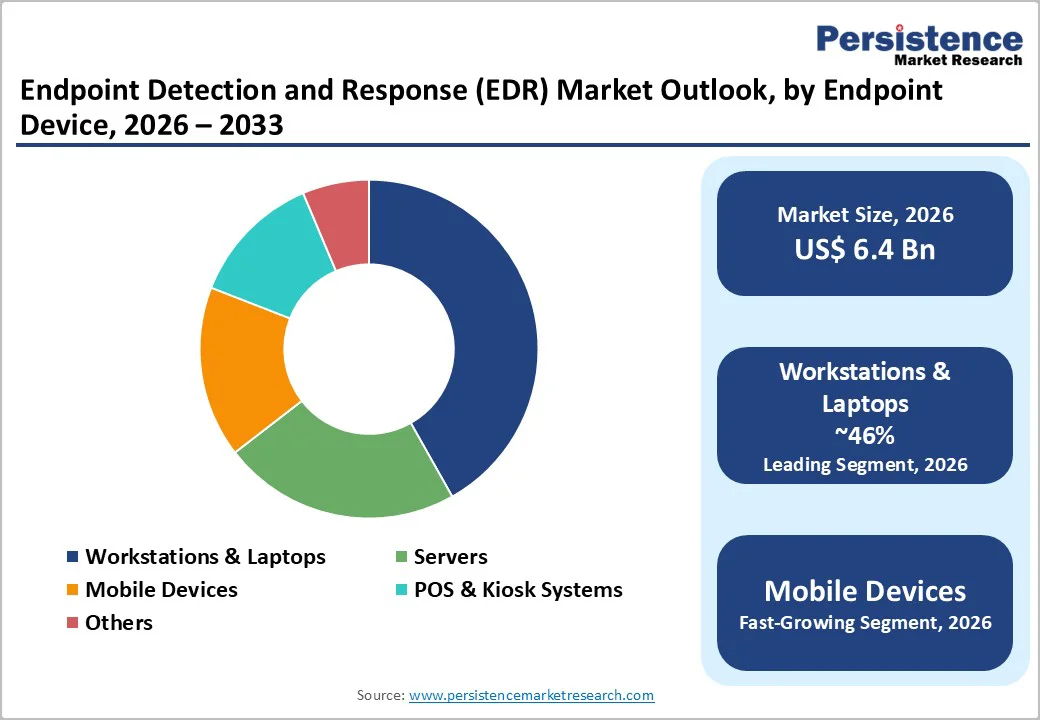
Endpoint Device Analysis,
Workstations and laptop computers remain the dominant endpoint category, representing 46% of 2026 market value at US$ 2.9 Bn. This leadership reflects the prevalence of traditional computing devices in enterprise environments and their criticality in organizational operations. The commercial viability of EDR solutions was initially established through workstation and laptop protection, creating established procurement categories, IT operational processes, and security team expertise focused on these endpoints. Large enterprises maintain heterogeneous endpoint populations spanning thousands to hundreds of thousands of workstations, creating substantial market opportunity for vendors offering scalable, lightweight agent architectures that minimize performance impact on user computing experience.
Mobile device protection is the fastest-growing endpoint category, expanding at 28.1% CAGR, reflecting organizational acceptance of smartphones and tablets as business-critical endpoints requiring security controls equivalent to traditional computing devices. The proliferation of mobile-first workforces in emerging markets, particularly across Asia Pacific, India, and Southeast Asia, has fundamentally altered endpoint security requirements. Contemporary mobile threats including mobile malware, credential theft, and data exfiltration through compromised applications now demand endpoint-level detection and response capabilities previously reserved for computing devices.
Enterprise Size Analysis,
Large enterprises currently represent 61% of market value at US$ 3.9 Bn, reflecting higher security requirements for organizations managing sensitive intellectual property, customer financial information, and critical operational systems. Large enterprises typically operate global endpoint populations spanning multiple geographic markets, requiring vendors to provide multi-regional deployment capabilities, localized threat intelligence, and compliance expertise across diverse regulatory frameworks. The procurement processes for large enterprises are established and competitive, with vendors competing on technical capabilities, ecosystem integration, threat intelligence quality, and operational support.
Small & Medium Enterprises (SMEs) represent the fastest-growing category, expanding at 29.4% CAGR, driven by regulatory mandates applying equally to organizations of all sizes, increased availability of simplified EDR solutions suitable for smaller endpoint populations, and growing security awareness among SME leadership. Federal regulatory mandates affecting SME contractors, insurance companies offering cyber coverage contingent upon EDR deployment, and business partner requirements create procurement drivers that overcome traditional cost objections.
Industry Analysis,
BFSI is expected to hold over 28% market share in 2026, reflecting these organizations' regulatory exposure, sensitivity to data breach risk, and concentration of valuable assets requiring sophisticated endpoint protection. Financial institutions operate under strict regulatory frameworks including PCI-DSS (payment card industry standards), SEC Regulation S-P (broker-dealer cybersecurity), and Office of the Comptroller of the Currency (OCC) guidance requiring endpoint-level threat detection as baseline security controls.
Healthcare represents the fastest-growing industry, expanding at 28.6% CAGR, driven by accelerating ransomware activity targeting the sector and increasingly stringent regulatory requirements. The healthcare sector experienced 389 ransomware incidents in 2024 affecting 45 million patient records, driving HIPAA modernization initiatives that now emphasize continuous endpoint monitoring as a foundational security requirement. Organizations face unusual threat dynamics where cyber incidents directly impact patient safety ransomware disabling clinical systems delay treatment, divert emergency patients to competing facilities, and in extreme cases cause patient harm.
North America Endpoint Detection and Response (EDR) Market Trends
North America maintains 36% of global EDR market share, reflecting early technology adoption, substantial organizational IT security budgets, and the region's role as the regulatory standard-setter for global cybersecurity practices. The U.S. market specifically drives North American dominance through the convergence of advanced cybersecurity infrastructure, substantial enterprise IT budgets, early EDR adoption among technology companies and financial institutions, and stringent regulatory mandates. Regulatory drivers, including CMMC expansion to broader contractor ecosystems, SEC enhanced cybersecurity disclosure requirements, and state privacy laws are expected to sustain North American EDR demand.
Asia Pacific Endpoint Detection and Response (EDR) Market Trends
Asia-Pacific is expected to grow at the highest rate with a CAGR of 29%, driven by rapid digital transformation, cloud adoption acceleration, proliferation of cybercrime originating from the region, and emerging regulatory frameworks establishing EDR requirements. China, India, and Japan represent the three primary growth engines within Asia-Pacific China's digital economy expansion and regulatory mandates establish procurement requirements for organizations handling Chinese resident data; India's emergence as a software development and IT services center creates demand for EDR solutions protecting technology talent and intellectual property; and Japan's mature financial services sector and manufacturing base demand sophisticated endpoint protection. The region's IT and technology companies are rapidly adopting EDR solutions, establishing domestic market presence that accelerates broader regional adoption among financial, healthcare, and government organizations.
Europe Endpoint Detection and Response (EDR) Market Trends
Europe holds more than 25% global market share and drives second-largest geographic EDR spending, with regulations including the General Data Protection Regulation (GDPR) establishing mandatory endpoint protection frameworks for all organizations processing EU resident data. GDPR's explicit requirements for technical and organizational measures to safeguard personal data, combined with 72-hour breach notification timelines and penalties reaching €20 million or 4% global revenue, have driven rapid EDR adoption across European enterprises regardless of industry. Regulatory harmonization within Europe has created unified procurement requirements supporting efficient market coverage by EDR vendors.
The EDR market exhibits a consolidated competitive structure, with the five largest vendors collectively controlling approximately 45-55% of the global market share. This concentration reflects significant barriers to competitive entry, including substantial research and development investment requirements, complex multi-platform agent development, and the network effects of threat intelligence scale that limit new entrant viability. Leading vendors emphasize integration with complementary security and IT management platforms, recognizing that EDR operates within complex security infrastructure.
The global market is projected to be valued at US$6.4 Bn in 2026.
The urgent need to detect, investigate, and respond to increasingly sophisticated endpoint-based threats such as ransomware, fileless malware, and zero-day attacks in real time is a key driver of the market.
The market is expected to witness a CAGR of 23.8% from 2026 to 2033.
Growing adoption of AI- and machine-learning–driven EDR platforms, cloud-native and XDR-integrated solutions, is creating strong growth opportunities.
CrowdStrike Holdings, Inc., Microsoft Corporation, SentinelOne, Inc., Palo Alto Networks, Inc., Trend Micro Inc. are among the leading key players.
| Report Attribute | Details |
|---|---|
|
Historical Data/Actuals |
2020 – 2025 |
|
Forecast Period |
2026 – 2033 |
|
Market Analysis Units |
Value: US$ Bn/Mn, Volume: As Applicable |
|
Geographical Coverage |
|
|
Segmental Coverage |
|
|
Competitive Analysis |
|
|
Report Highlights |
|
|
Customization and Pricing |
Available upon request |
By Solution
By Deployment
By Endpoint Device
By Enterprise Size
By Industry
By Region
Delivery Timelines
For more information on this report and its delivery timelines please get in touch with our sales team.
About Author